Blockchain governance - Part 5
Part 5: Assessing blockchain governance
Blockchain security is paramount to implement good governance otherwise stakeholders’ decisions could be reverted. A secure protocol depends on adequate blockchain architecture, secure hashing functions and cryptographic primitives, transparency, privacy and decision-making mechanisms. Good security controls must be cheap to implement and costly to attempt to bypass or violate as a way of deterring dishonest adversaries.
Methodology
This articles series used publicly available data from Decred and Bitcoin blockchains. For Decred, the data was obtained from PostgreSQL database used in dcrdata1, the free, open source block explorer. For Bitcoin, the data was obtained from Blockchain.com. Price information in USD was obtained from Yahoo Finance2,3. For next section, ‘Simulation: the InvalidationGame’, the probability distribution used inside the script was obtained from the above PostgreSQL database. For the other section, ‘Security increases opportunity cost’, the calculations used data obtained from the sources above. For Part 6 - Testing governance hypotheses, all data was obtained from dcrdata and Yahoo Finance and was processed using R.
The next section uses the InvalidationGame, a Python script developed for this analysis, to simulate PoW and PoW+PoS attacks with the intent to show the difference in time and cost of such attacks. Section ‘Security increases opportunity cost’ analyses the attacks from Capex and Opex perspective to understand how much does an attack cost in dollar figures. Part 6 - Testing governance hypotheses analyses data from dcrdata database, testing several hypotheses to assess Decred governance (security, issuance predictability, scarcity, incentives, voting) and Part 7 - Assessment results summarises the findings and concludes.
Simulation: the InvalidationGame
The security provided by the two-factor authentication mechanism of PoW+PoS implemented by Decred can be better understood in a simulation. For that purpose, it is developed the InvalidationGame4, a Python script that simulates a double-spending attack to show the probability of success of an attack when perpetrated against a pure PoW blockchain and also against a PoW+PoS one. It is assumed to be a double-spending attack because attacks cost upfront money (PoW) and the adversary attacking the network must have economic incentives to execute the attack. A double-spending attack is an attempt to spend the same coin5 more than once. The attacker would spend a coin in a regular transaction and then try to mine blocks that would exclude that transaction from the blockchain, creating a blockchain fork. The chain with more blocks, being 6 blocks a generally accepted number because of Bitcoin reference client, is the one considered the single source of truth because it is the result of the work of the majority of nodes (Bonneau, et al., 2015).
Other possible scenarios would be:
- the sabotage performed by wealthy adversaries, like governments;
- an adversary mining empty blocks
Stakeholders can withhold a miner’s reward invalidating blocks even if the block conforms to the consensus rules of the network. This disincentivises bad behaviour such as miners mining empty blocks or attempting double-spending attacks. For double-spending attacks, two assumptions must be considered: first “we consider the scenario of an attacker trying to generate an alternate chain faster than the honest chain. Even if this is accomplished, it does not throw the system open to arbitrary changes, such as creating value out of thin air or taking money that never belonged to the attacker. Nodes are not going to accept an invalid transaction as payment, and honest nodes will never accept a block containing them. An attacker can only try to change one of his own transactions to take back money he recently spent.” (Nakamoto, 2008, p. 7). The other is an opportunity cost because a greedy attacker with substantial hashpower would have to choose between trying to perform a double-spending attack or participating as an honest node and generate new coins. (Nakamoto, 2008, p. 4).
The results shown in Tables 1-3 come from the execution of the InvalidationGame and assume that A0 represents the honest adversaries while A1 represents an adversary trying to reverse a transaction (the double-spending attack), but it makes no difference to the calculations if the roles are inverted. Hashpower simulates the probability of mining a block while Stake simulates the percentage of PoS tickets. For all simulations it is assumed that the adversary just spent a transaction and started a double-spending attack.
Tables 1 and 2 show two scenarios: in the first, adversary A0 has 90% of hashpower and A1 has a small amount (10%), and in the second, adversary A1 has about the same hashpower (55%) as the honest nodes represented by A0 (45%). In the first scenario it took, in average, 3.2771 blocks for an adversary to have a 2-block advantage over the other and 7.8240 blocks in average for a 6-block advantage, when the simulation ended. In the second the numbers were 6.7431 and 38.4911 blocks for 2-block and 6-block advantage. The numbers are higher in the second scenario because the adversaries have almost the same probability of mining a block (45% against 55%), taking longer for them to establish the generally accepted advantage of 6 blocks over the other.
The 2-block advantage is shown in an article (Grunspan & Pérez-Marco, 2019) that tries to demonstrate that the double-spending attack is already unfeasible much sooner than the generally acceptable 6-block confirmation because it becomes unprofitable in 2 blocks, leading to the ruin of the attacker. The last line of the simulation output informs that the losing adversary is forgoing a block reward in valid blocks by trying to double-spend. Another cost, not mentioned in the tables, is the ‘cost of doing business’, that is the cost related to working on a block and having an adversary successfully mine it (and get the block reward).
| Adversary | Hashpower | Simulations won | Simulations won |
|---|---|---|---|
| A0 | 90.00% | 98681 | 98.681% |
| A1 | 10.00% | 1319 | 1.319% |
On average, 2-block and 6-block advantage reached in: 3.2771 and 7.8240 blocks
Attack cost, on average: 0.7486 PoW block reward
Number of simulations: 100000; Average: 0.0012 seconds, Total: 00:19:54
Table 1 – Result of 100 000 90%/10% PoW simulated attacks
Source: own elaboration
| Adversary | Hashpower | Simulations won | Simulations won |
|---|---|---|---|
| A0 | 45.00% | 26270 | 26.27% |
| A1 | 55.00% | 73730 | 73.73% |
On average, 2-block and 6-block advantage reached in: 6.7431 and 38.4911 blocks
Attack cost, on average: 22.3953 PoW block rewards
Number of simulations: 100000; Average: 0.0110 seconds, Total: 00:35:50
Table 2 – Result of 100 000 45%/55% PoW simulated attacks
Source: own elaboration
While Tables 1 and 2 show the result of attacks in pure PoW blockchains, Table 3 shows an attack on a PoW+PoS blockchain, where the honest nodes (A0) have 45% of hashpower and 70% of PoS tickets. Although the dishonest adversary (A1) has more hashpower, the honest nodes have more tickets and will not validate blocks that contain double-spending transactions.
| Adversary | Hashpower | Stake | Sims won | Sims won | Avg Invalid Blocks | Avg Valid Blocks |
|---|---|---|---|---|---|---|
| A0 | 45.00% | 70.00% | 84122 | 84.122% | 1.6495 | 7.8575 |
| A1 | 55.00% | 30.00% | 15878 | 15.878% | 9.7451 | 1.8594 |
On average, 2-block and 6-block advantage reached in: 3.8929 and 10.7169 blocks
Attack cost, on average: 1.8594 PoW block rewards, due to PoS invalidation
Number of simulations: 100000; Average: 0.077 seconds, Total: 04:03:16
Table 3 – Result of 100 000 45%/55% PoW + 70/30 PoS simulated attacks
Source: own elaboration
Table 3 shows that A1 forgo rewards for 9.7451 blocks in average due to blocks that were invalidated by the honest nodes. But the cost is even higher: some blocks mined (PoW) and validated (PoS) by A1 were left in an unextended blockchain fork because the honest nodes were able to extend their own chain in z blocks, and such chain has no block mined by A1 since the attack began. Hence the adversary also forgoes rewards for 1.8594 validated blocks, in average.
Security increases opportunity cost
A strong authentication mechanism increases the cost of an attack, which can be measured in dollar figures. To perform an attack against a PoW blockchain the attacker must i) rent the equipment; or ii) buy the equipment and build/rent the facilities and only then start an attack by spending electricity. An attack against a PoW+PoS blockchain includes also the cost of owning the coins (or cryptoassets) and such attack may devalue those coins, increasing the risk for the attacker.
Attacks can be internal or external: internal attacks happen when miners decide to perform an attack using current equipment. Because there is no central registration authority, individual miners would have to meet in forums or mining pools to reach consensus on such attack. Mining pools themselves could also be considered adversaries in case they decide to use the PoW they command to attack networks. An adversary may also rent mining devices to perform a short-term attack on a number of blockchains supported by the cloud mining provider. In an internal attack there is no increase in the number of equipment or total hashpower of the network. An external attack assumes that an adversary buys new equipment, thus increasing the processing power of the network. The adversary must account for the rapid depreciation of such devices, not only when it comes to product lifespan but also because new devices will render these devices inefficient.
Hashpower is estimated as shown in equation 4.1, taking the network difficulty informed by the blockchain protocol and the block time in seconds (600 seconds for Bitcoin, 300 seconds for Decred). Network difficulty measures how difficult it is to find the hash for a block under a certain target to keep blocks being generated within a certain amount of time.
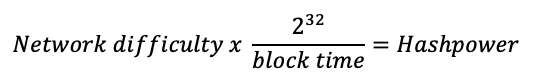
Equation 4.1 - Hashpower calculation formula
Source: (Bitcoin Community, 2017)
As previously explained in Part 4, subsection ‘Decred Project approach’, an attacker would require a combination of tickets and hashpower to obtain enough power to revert blocks mined by the honest nodes. Equation 4.2 shows how to calculate the probability of an attacker holding a majority of selected tickets knowing that the attacker controls fraction y of the tickets in the pool. In Decred network N is always 5 because every block draws a maximum of 5 tickets and k is the number tickets between N tickets the attacker might have. The participation ratio p will be assumed to be 1 because in Decred a majority of voters is usually online (Table 24 in Part 6 has the numbers). Equation 4.3 calculates how much hashpower the attacker would need as a multiplier of the honest adversaries’ hashpower given that the attacker has a probability P(y) of having a majority of tickets drawn. Figure 4 shows the Security Curve as a result of the PoW+PoS authentication mechanism.
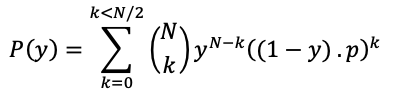
Equation 4.2 - Probability of an attacker holding a majority of selected tickets (PoS)
Source: (Stafford, 2019)
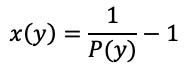
Equation 4.3 - Attacker’s required hashpower (PoW) to outpace the honest adversaries
Source: (Stafford, 2019)
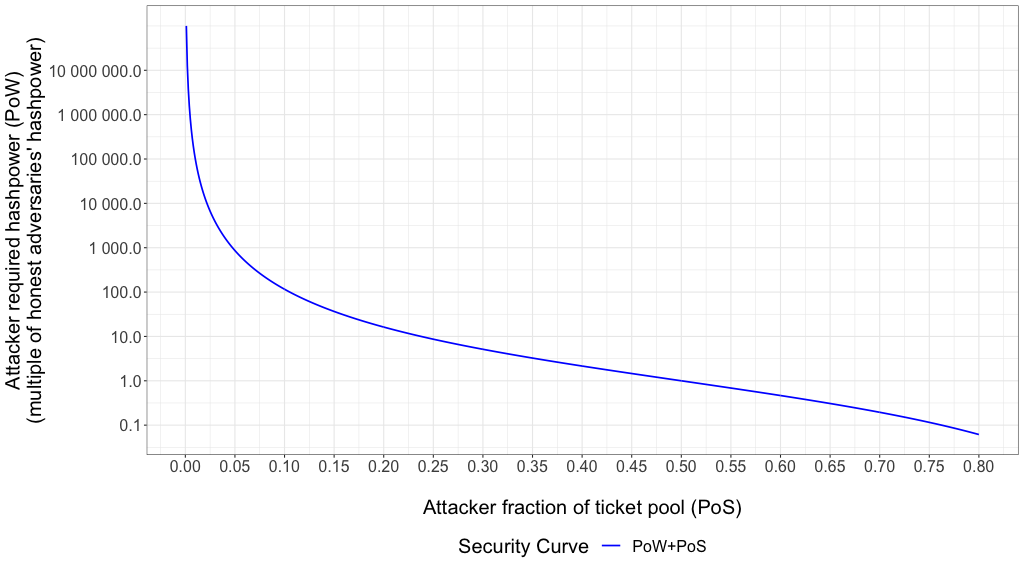
Figure 4 – Security curve created by PoW+PoS combined authentication
Source: own elaboration
Any adversary with a combination of PoW + PoS power at the left of the security curve is considered safe to the security of the blockchain. As detailed in the beginning of this section, the following analysis assumes the point x=0.5, y=1.0 in the security curve, which means that the dishonest adversary has one time the hashpower of the honest adversaries (50% of the total) and 50% of all tickets in the pool (the ‘majority attack’).
External/internal attack
This section presents the cost of an external/internal attack where the adversary is 0% invested in either coin: the attacker buys equipment from vendors (external) and coins from traders or miners using fiat money (internal), both at market price and until the attacker reaches 50% of PoW equipment (increasing the number of equipment by a factor of 1) and 50% of the issued coins (Decred only) without increasing the exchange rate, which is an unrealistic assumption because it assumes that current ticket owners will sell half of their Decred otherwise the adversary would have to buy all Decred available (Decred not locked up in tickets, 49.84% of all issued coins on 10 Feb 2020) without skyrocketing its price.
The cost of an external PoW + internal PoS attack against Decred blockchain considers hashpower, coin price, current equipment, ticket price in DCRs (estimated as an internal attack), facility cost estimation and electricity price on 10 Feb 2020.
| Equation | Operation | Amount | Unit |
|---|---|---|---|
| (A) | ASIC device: DCR5 (34 Th/s, 1 610W, USD 1 282) | 34 | Th/s |
| (B) | Decred network hashpower on 10 Feb 2020 | 450 150 | Th/s |
| (C = B/A) | ASIC devices for 1x attack (more 450 150 Th/s) | 13 240 | unit |
| (D = 1 610W * C) | ASIC devices will spend 1 610W * 13 240 units | 21 316 | kWh |
| (E = USD 1 282 * C) | Cost to buy 13 240 DCR5 units | 16 973 680 | USD |
| (F = USD 0.05 * D) | Cost of electricity in Iceland (USD 0.05/kWh) | 1 066 | USD/h |
| (G = 0.05 * E) | Assuming facility costs (5% of device cost) | 848 684 | USD/h |
Table 4 – Decred Proof-of-Work equipment and network hashpower
Source: own elaboration
| Equation | Operation | Amount | Unit |
|---|---|---|---|
| (H) | Ticket pool size in DCRs | 5 558 457 | DCR |
| (I = 0.5 * H) | 50% PoS attack would require N DCRs | 2 779 229 | DCR |
| (J = 21.13 * I) | Cost to buy 2 779 229 DCR at price USD 21.13 | 58 725 109 | USD |
Table 5 – Decred Proof-of-Stake cost of (internal) attack
Source: own elaboration
| Equation | Operation | Amount | Unit |
|---|---|---|---|
| (E + J) | Capex: USD 58 725 109 (PoS) + USD 16 973 680 (PoW) | 75 698 789 | USD |
| (F + G) | Opex: 1 066 USD/h + 848 684 USD/h (PoW) | 849 750 | USD/h |
Table 6 – Total cost (PoW + PoS) of an attack against Decred on 10 Feb 2020
Source: own elaboration
The cost of an external attack against Bitcoin blockchain considers hashpower, current equipment, facility cost estimation and electricity price on 10 Feb 2020:
| Equation | Operation | Amount | Unit |
|---|---|---|---|
| (A) | ASIC dev: Antminer S17+ (73 Th/s, 2 920W, USD 2 580) | 73 | Th/s |
| (B) | Bitcoin network hashpower on 10 Feb 2020 | 107 525 520 | Th/s |
| (C = B/A) | ASIC devices for 1x attack (more 107 525 520 Th/s) | 1 472 953 | unit |
| (D = 2 920W * C) | ASIC devices will spend 2 920W * 1 472 953 units | 4 301 022 760 | kWh |
| (E = USD 2 580 * C) | Cost to buy 1 472 953 S17+ units: 1 472 953 * USD 2 580 | 3 800 218 740 | USD |
| (USD 0.05 * D) | Cost of electricity in Iceland (USD 0.05/kWh) | 215 051 138 | USD/h |
| (0.05 * E) | Assuming facility costs (5% of device cost) | 190 010 937 | USD/h |
Table 7 – Bitcoin Proof-of-Work equipment and network hashpower on 10 Feb 2020
Source: own elaboration
| Equation | Operation | Amount | Unit |
|---|---|---|---|
| (C) | Capex (PoW) | 3 800 218 740 | USD |
| (D + E) | Opex: 190 010 937 USD/h + 215 051 138 USD/h (PoW) | 405 062 075 | USD |
Table 8 – Total cost (PoW) of an attack against Bitcoin on 10 Feb 2020
Source: own elaboration
Considering a majority attack (50% +1) and the information on Tables 9 and 10, Decred would be more expensive than Bitcoin to attack on 10 Feb 2020 if one of two conditions were true: 1) DCR price in USD (exchange rate) were 64.43 times the value at the time 2) Decred network size (hashpower) were 220.45 times the level at the time
If Decred network had the same hashpower as Bitcoin network, an attack on Decred network would cost 1.0823x an attack on Bitcoin network. If Decred network had the same hashpower as Bitcoin network and if Decred were priced at the same exchange rate as Bitcoin, an attack on Decred would cost 8.2753x an attack on Bitcoin.
| Fiat exchange rate | Coin Supply | Exchange rate | ||
|---|---|---|---|---|
| BTCUSD | 9 856.61 | 18 209 137 | 466.4747 | DCRBTC |
| DCRUSD | 21.13 | 11 081 717 | 0.0021 | BTCDCR |
Table 9 – Decred and Bitcoin supply and exchange rates on 10 Feb 2020
Source: own elaboration
| _ | Network size in Th/s on 10 Feb 2020 | Network size in scale |
|---|---|---|
| Decred | 450 150 Th/s | 0.0042 x Bitcoin size |
| Bitcoin | 107 525 520 Th/s | 238.8660 x Decred size |
Table 10 – Decred and Bitcoin network size (hashpower) in Th/s on 10 Feb 2020
Source: own elaboration
Considering coin supply and exchange rates from Tables 9 and 10, the calculation results from Tables 6 and 8, and one very important restriction to this model that assumes that Decred stakeholders would sell up to 50% of their coins at market price, Table 11 shows that Bitcoin is more expensive to attack than Decred on 10 Feb 2020.
| Most expensive blockchain to attack on 10 Feb 2020: | Bitcoin |
|---|---|
| Decred | 0.0199 x than Bitcoin |
| Bitcoin | 50.2019 x than Decred |
Table 11 – Most expensive blockchain to attack on 10 Feb 2020
Source: own elaboration
Internal/internal attack
An internal attack means that no additional mining devices are being added to the network. It could be current PoW miners performing a short-term attack on the network, but it is also possible to rent mining devices in the ‘cloud’. ‘Cloud’ means companies that rent datacentre capacity as a service on the Internet where the customer pays only for used capacity (Opex) without the need to also build the datacentre, buy computing and networking devices (Capex) and pay to operate them (Opex). Nicehash6 is one of these cloud mining companies renting processing power for some hashing algorithms. Crypto517 website calculates the cost of 1h attack for several PoW cryptocurrencies and how much hashrate Nicehash cloud offers to perform a majority attack, allowing an adversary to pay only for the marginal cost of the hashrate. This website informs that Nicehash currently has 0% hashrate rental capacity for Bitcoin and Decred is not currently available in their list because it is a PoW+PoS cryptocurrency and PoS is one their recommended solutions to reduce the risk of a majority attack.
Although it is possible to rent PoW mining devices to perform attacks against almost any blockchain (assuming there is available hashrate for rental), Decred also requires the attacker to buy coins in order to acquire tickets (unless the attacker is willing/able to rent a multiple of the hashrate required to attack the network with less PoS voting power as shown in the Security Curve of Figure 4). Decred does not operate with a Delegated Proof-of-Stake (DPoS) system where the ticket owner can delegate its voting power to a mining pool or a Voting Service Provider (VSP), which could in turn override stakeholder’s wishes and vote as it see fit, nor it would be possible to rent PoS voting power from ticket owners because of the pseudo random drawing mechanism.
Table 12 assumes an internal PoW attack for both Bitcoin and Decred with an internal PoS attack for Decred (which will not increase the number of locked DCRs in tickets), in the same unrealistic assumption that current ticket owners will sell half of their Decred at market price, and Table 13 shows how many times one blockchain is more secure than the other considering an internal attack and using a ratio of the total cost of attacks:
Considering the scenario presented at the beginning of this section, where the dishonest adversary has slightly more power than the honest nodes (50% +1 of PoW devices and PoS tickets), Tables 12 and 13 show the result of 100 000 simulations for this setup for both attacks scenarios.
| Equation | Operation | Amount | Unit |
|---|---|---|---|
| (K) | Decred Capex: USD 58 725 109 (PoS) | 58 725 109 | USD |
| (F + H) | Decred Opex: 1 066 USD/h + 1 178 USD/h (PoW) | 2 244 | USD/h |
| (F + H + K) | Decred Total 1-hour attack cost | 58 727 353 | USD |
| (24 *(F + H) + K) | Decred Total 1-day attack cost | 58 778 965 | USD |
| (120 *(F + H) + K) | Decred Total 5-day attack cost | 58 994 485 | USD |
| (Q + S) | Bitcoin Opex: 215 052 USD + 263 904 USD (1-hour attack) | 478 971 | USD/h |
| (24 * (Q + S)) | Bitcoin Total 1-day attack cost | 11 495 304 | USD |
| (120 * (Q + S)) | Bitcoin Total 5-day attack cost | 57 476 522 | USD |
Table 12 – Total cost of internal/internal attacks on 10 Feb 2020
Source: own elaboration
Table 13 shows that Decred is more expensive to internally attack than Bitcoin on 10 Feb 2020.
| Most expensive to attack | 1 hour | 1 day | 5 days | . |
|---|---|---|---|---|
| Decred (internal/internal) | 122.6115 | 5.1133 | 1.0264 | x than Bitcoin |
| Bitcoin (internal) | 0.0081 | 0.1956 | 0.9743 | x than Decred |
Table 13 – Most expensive to attack (internal/internal) on 10 Feb 2020
Source: own elaboration
Table 13 shows only the cost of an internal attack, not its rewards. Moroz explains8 the game rewards by introducing the work of Budish where the attacker has access to hashrate rental market, which could render the attack free, cheap or impossible, depending on rental prices and availability (Budish, 2018). Moroz et al. demonstrate in Equation 4.4 that in a competitive miner economy (under certain conditions of hashrate price and availability), the cost spent in an attack is cancelled by its block rewards, driving the attack cost to zero. Then, being able to execute a ‘free’ attack, the attacker’s profit derives from the double- spend.
Reward per block = Total expenditure to mine a block
𝑃b = hash per block x cost per hash
For e blocks:
Cost of length 𝑒 attack – Block rewards for 𝑒 blocks = 0
𝑒𝑃 −𝑒𝑃 = 0
Equation 4.4 - Source: Modified from (Moroz, Aronoff, Narula, & Parkes, 2020)
Moroz et al. conclude arguing that the security of a PoW blockchain comes from making the net cost attack greater than its profit, but with a net cost attack of zero shown in Equation 4.4, any profit will be greater. PoW blockchain security becomes then closely related to the difficulty (or impossibility) of renting large hashrates due to unavailability of such amounts or price slippage in rental market.
In the same line of argument, Auer argues that in the long run all pure PoW blockchain security will be low because they will depend exclusively on transaction fees when block rewards will be low or non-existent, and these transaction fees will only be high in times of network congestion (Auer, 2019). We may conclude that with less honest miners, it will be easier to reach majority by renting mining hashrate for blockchains that share hashing algorithms. This argument is used by Hasu et al. to suggest a highly contentious 1% annually perpetual coin issuance, which instead of adding inflation and decreasing purchasing power would actually increase purchasing power and reduce uncertainty over miner revenues by adding security through miner incentives (Hasu, Prestwich, & Curtis, 2019).
For Hasu et al. a successful attack might reduce the price of the underlying digital asset and thus miners are incentivised not to lease mining hardware to potential attackers while at the same time, depending on their skin in the game, holders are more likely to pay the cost of a social coordination (to counterattack). Instead, Lovejoy provided empirical data9 that argues the opposite of the generally accepted expectation that prices would drop: for less prominent coins, the media exposure may have outweighed the loss of confidence keeping their prices levelled (or even higher) a month after the attack, but it is not possible to assume the same outcome for more prominent coins, like Bitcoin, where their value may derive from an expectation of security from these attacks (Lovejoy, 2020). This expectation of security counterarguments the hypothesis of buying Decred to acquire tickets, perform the double- spend attack and then try to sell Decred at a price close to buy price due to market slippage, possible devaluation caused by the attack and because tickets may take as long as 143 days to be drawn.
Using the same argument of skin in the game used by Hasu et al., and extending Budish model (Budish, 2018), Moroz et al. showed that the victim may also retaliate, if there is available hashrate capacity for rental, because the victim has more at stake (the value of the original transaction) than the attacker (Moroz, Aronoff, Narula, & Parkes, 2020). These arguments help show the strength of the PoW+PoS security mechanism.
Majority attack simulation
Considering the scenario presented at the beginning of this section, where the dishonest adversary has slightly more power than the honest nodes (50% +1 of PoW devices and PoS tickets), Tables 14 and 15 show the result of 100 000 simulations for this setup for both attacks scenarios. The PoW simulation took 32min25secs while the PoW+PoS simulation took 7h02min, which indicates the increase in cost to attack such networks.
| Adversary | Hashpower | Simulations won | Simulations won |
|---|---|---|---|
| A0 | 49.99% | 50037 | 50.0370% |
| A1 | 50.01% | 49963 | 49.9630% |
On average, 2-block and 6-block advantage reached in: 7.0091 and 55.0898 blocks
Attack cost, on average 36.0709 PoW block rewards
Number of simulations: 100000; Average: 0.0120 seconds, Total: 00:32:25
Table 14 – Result of 100 000 49.99%/50.01% PoW simulated attacks
Source: own elaboration
| Adversary | Hashpower | Stake | Sims won | Sims won | Avg Invalid Blocks | Avg Valid Blocks |
|---|---|---|---|---|---|---|
| A0 | 49.99% | 49.99% | 49785 | 49.7850% | 18.7086 | 17.9623 |
| A1 | 50.01% | 50.01% | 50215 | 50.2150% | 18.6579 | 18.0050 |
On average, 2-block and 6-block advantage reached in: 4.9870 and 36.9674 blocks
For A1, the attack cost, on average: 18.0050 PoW block rewards, due to PoS invalidation
Number of simulations: 100000; Average: 0.2092 seconds, Total: 07:02:19
Table 15 – Result of 100 000 49.99%/50.01% PoW+PoS simulated attacks
Footnotes
1 dcrdata, available at https://github.com/decred/dcrdata
2 Bitcoin USD price, available at https://finance.yahoo.com/quote/BTC-USD/history?period1=1454716800&period2=1586131200&interval=1d&filter=history&frequency=1d
3 Decred USD price, available at https://finance.yahoo.com/quote/DCR-USD/history?period1=1454716800 &period2=1586131200&interval=1d&filter=history&frequency=1d
4 InvalidationGame, https://github.com/mmartins000/invalidationgame
5 Actually, due to the ledger inner workings, the attacker tries to spend the same transaction more than once. A transaction corresponds to an amount of coins, like a check.
6 Available at https://www.nicehash.com/.
7 Available at https://www.crypto51.app/.
8 “Double-Spend Counter-Attacks: Threat of Retaliation in PoW Systems”, available at https://www.youtube.com/watch?list=PLKCUhIiFc_PfT_9IlARL2LZmXaAIthE_n&v=lKd-AoDyFlA.
9 “51% attacks”, available at https://dci.mit.edu/51-attacks.
References
Bonneau, J., Miller, A., Clark, J., Narayanan, A., Kroll, J. A., & Felten, E. W. (2015). SoK: Research Perspectives and Challenges for Bitcoin and Cryptocurrencies. 2015 IEEE Symposium on Security and Privacy. San Jose, CA, USA: IEEE. Retrieved from: https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=7163021
Grunspan, C., & Pérez-Marco, R. (2019, Dez 12). On probability of Nakamoto double spend. Retrieved from Arxiv: https://arxiv.org/abs/1912.06412
Nakamoto, S. (2008, October 31). Bitcoin: A peer-to-peer electronic cash system. Retrieved from Nakamoto Institute: https://nakamotoinstitute.org/bitcoin/
Stafford, B. (2019). Parametrized cost of attack as a measure of Decred network security.