Blockchain governance - Part 4
Part 4
Decred Project
Decred is an open, progressive, and self-funding cryptocurrency with a system of community-based governance integrated into its blockchain. Decred is bound by a set of rules, which include guiding principles, a system of governance – Politeia – and a funding mechanism – the network fund (Decred Project, 2016).
Decred fundamentals and money issuance
Decred blockchain server (dcrd) is a fork from Bitcoin blockchain server (btcd) from btcsuite Bitcoin package, created by Decred developers previously to Decred existence. Source code forking is different from blockchain forking, depicted in Figure 2 on section 2.5. A source code fork means that a copy of the original code was made (Martins, 2018).
On 08 Feb 2016, on block #1, 1 680 000 DCR were pre-mined: 840 000 DCRs (50%) were distributed among developers as a form of payment and the other 840 000 were distributed via airdrop, with 282.63795424 DCR sent to each one of 2 972 email addresses who subscribed to the airdrop list, a form of distribution that developers created so that since the beginning there would be a circulation of DCRs (supply and demand), diluting the participation of the initial developers (Martins, 2018). Equation 3.1 shows how total Decred issuance is calculated. On Decred creation, on 08 Feb 2016, each mined block could reward the participants (PoW and PoS miners and the treasury) with a maximum total of 31.19582664 DCR. After every 6 144 blocks, the issuance is exponentially reduced a factor of (100⁄101)^n, a process repeated 400 times until June 2039. By this date, this issuance cycle, added to the initial 1 680 000 pre-mined DCRs, is supposed to issue1 an estimated amount of 20 638 308 DCRs (Martins, 2018).
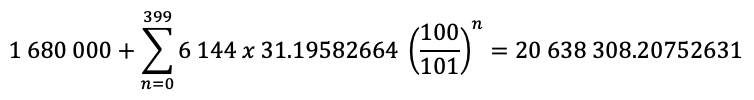
Equation 3.1 - Decred estimated issuance equation (until June 2039)
Source: (Martins, 2018)
Bitcoin and Decred will issue each one almost 21M coins in their blockchains, but estimates show that Decred will have issued all of its coins by September 2120, with an upper supply limit of 20 999 999.99800912, while Bitcoin will still be ‘printing money’ until 2140. Equation 3.1 shows an estimate for Decred after reducing its block reward 400 times, approximately every 21.33 days, while Bitcoin takes almost 4 years to reduce by half its issuance of money (every 210 000 blocks, as shown in equation 3.2 below), an event called ‘halving’ which has a great impact in crypto financial markets. Figure 3 shows a comparison between their supply growth curves (based on equations 3.1 and 3.2) and it is noticeable that Decred curve has a smoother reduction in its issuance.
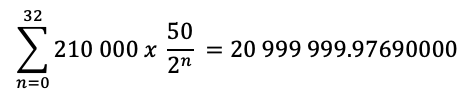
Equation 3.2 - Bitcoin estimated issuance equation
Source: Modified from (Bitcoin Community, 2017)
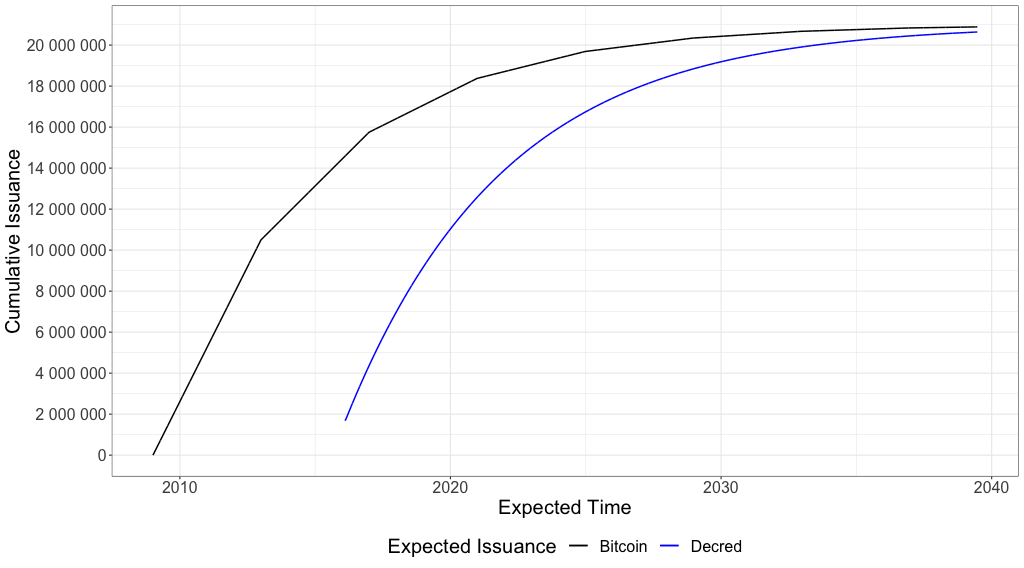
Figure 3 – Bitcoin and Decred estimated supply growth curves until June 2039
Source: own elaboration
Blockchain security
There is no good governance without security. If the rules are vague or cannot be correctly enforced, if the consensus mechanism does not prevent actors from playing a dominant role, if the voting system is insecure or if there is no transparency, accountability, and anonymity, it is not possible to guarantee the integrity of electoral outcomes (Johnson, 2019). Without the correct checks and balances there is no governance or democracy. Also, knowing that there is ‘no free lunch’ and that running a distributed ledger system that helps reduce uncertainties and voting irregularities comes with a cost, the incentives must be clear and well-balanced to avoid dominance and public distrust. This is why scarcity (money issuance and inflation) and rewards are central issues, especially for public permissionless blockchains.
Proof-of-Work/Proof-of-Stake hybrid mining
PoW/PoS hybrid mining is critical to the understanding of the security mechanism of Decred blockchain, so a brief introduction is necessary. For consensus mechanisms that use only PoW a number of issues may arise, like denial of service via mining empty or artificially small blocks; censorship by ignoring certain transactions or addresses; and miners blocking or forcing consensus changes. There are disputes between miners, who want to centralize mining to increase their decision-making power and their profit to the detriment of the ecosystem; large companies and brokers, who seek to improve business-supporting features to increase their profit; and users and investors, who use the network for store of value and means of exchange. PoW mining can be seen as a single authentication factor for the consensus system, where it is usually executed by a small number of entities that do not necessarily represent the rest of the system participants. Although this process is fundamentally decentralized, practical issues lead the PoW mining process to be very centralized, similar to trusted third-party systems, like banks (Martins, 2018).
PoS mining creates a second-factor authentication, validating PoW mining decisions. Long-term stakeholders, those who wish to keep the coins, can vote on proposed changes to the network and their tickets validate the blocks mined via PoW. PoW miners get 60% of block reward, PoS miners receive collectively 30% and the remaining 10% goes to the treasury, also called the ‘network fund’. With PoS mining the coins are temporarily locked in the blockchain in exchange for tickets that have voting power.
The first phase involves a majority of PoW miners and PoS stakeholders upgrading their software to the latest version. For PoW, 95% of 1 000 last blocks must be in the latest version and for PoS, 75% of the votes in a 2 016-block interval must be the latest vote version (Decred Project, 2020). When the proposals are ready to be voted they show up at users’ software and miners and investors can choose how they will vote when they mine a block, or their ticket is drawn.
A deterministic pseudorandom lottery mechanism draws 5 tickets every block. Tickets vote on the validity of the previous block and are rewarded (in DCRs). A minimum of 3 tickets is necessary to validate the block and they are rewarded only if they actually cast their vote. The coins remain locked for 20 days, on average, but it could take as long as 143 days and 0.5% of the tickets expire after 143 days and do not get to vote and be rewarded, although the coins are released back but the fee paid to buy the ticket is not returned. Every block can contain up to 20 ticket purchases and prices are adjusted on 288-block windows to reduce2 the chance of large stakeholders buying huge amounts of tickets (Decred Project, 2020).
Network fund to reduce conflicts of interest
A source of funding is necessary to maintain a solid and steady development. This source of funding might be the developers, public donations or a private company and it makes a difference when assessing the possibility of conflict of interest, the agenda of each organisation and their objectives behind the funding.
Since 2014 entrepreneurs and scammers started using ICOs (Initial Coin Offering) to raise money to fund new cryptocurrency projects. It is estimated that 28.4 billion dollars were raised from January 2014 to August 2018. (Kalomeni, 2018). The term comes from the IPO (Initial Public Offering) and such projects suffer from conflicts of interest inherent to their funding model. “ICOs usually have two major problems: (1) on paper everything is possible; (2) to undertake is to build something first and then get the results, make a profit.” (Martins, 2018). Several projects never came to life, others had only the first commit of code to the code repository and after the funds were raised, they were abandoned.
To avoid relying on outside sources and agendas, Decred Project chose not to ask for the taxpayers’ money using innovation programmes nor started an ICO to be financed by third parties. Instead, Decred Project finances itself with 10% of every block reward.
PoW majority attack and the lack of ‘skin in the game’
The majority attack, also called ‘51% hashpower attack’, depends on an adversary being able to create blocks faster than the rest of the network (the honest nodes), maintaining the longest chain. The outcomes would be to create blocks without specific transactions allowing for the double-spending of a transaction previously spent by reversing the recent ledger history to defraud merchants, or carry out a denial-of-service attack by refusing to include transactions in the mined blocks, excluding participants from the network by denying them the ability to send or receive payments (Bentov, Lee, Mizhari, & Rosenfeld, 2014). This attack is feasible for wealthy adversaries and has great dependence on huge initial investment to acquire the mining equipment and on low fixed costs due to electricity and rent prices. Cloud-based attacks are not considered here because general purpose virtual machines do not calculate hashes efficiently as an ASIC mining device built for this specific purpose.
As stated in the previous section, a pure PoW system allows for bad decision-making: PoW miners can ‘mine and sell’, meaning that they can spend the reward in the next blocks or exchange it for fiat currency without being hurt in the long-term by the consequences of a bad decision made. With a pure PoW there is much less ‘skin in the game’, because miners can mine other coins that use the same PoW algorithm as their mining equipment.
Miners and the profit maximisation strategies
Part 2 explained that mining incentives can also be funded with transaction fees besides the block reward. To avoid the ‘tragedy of the commons’, a game theory problem where participants have an incentive to act selfishly to increase their own outcome in detriment of all other participants (Hardin, 1968), miners can select which transactions they will process based on the fees paid by the users. Otherwise, free riders would aim for no fee at all, which would reduce the incentives for miners to buy equipment and spend electricity validating the blocks, in the end reducing the number of participants and the security of the network, making everyone worse off than if they cooperated and paid their fees.
Each miner can select a minimum acceptable fee. They could cooperate to raise fees, but miners have an incentive to defect. Because mining is a capital-intensive business, and equipment prices, import taxes, building rents and electricity costs differ from place to place, miners operating with lower efficiency will have an incentive to accept lower fees in order to meet their point of equilibrium. If the miners select an excessively high fee, they may be left with only a handful of transactions and will have to bear the same processing costs to mine the block, so they have an incentive to choose the minimum acceptable fee that maximises their utility. During bear markets, when their coin exchange rate to fiat currency is even lower, they have to sell more coins to be able to break even. Wealthy miners operating with higher efficiency have incentives to manipulate the markets and lower the coin value, and consequently the exchange rate, to drive other miners off the market by pushing their revenue below their fixed costs.
Pure Proof-of-Stake systems
Proof-of-Stake ledgers are based on the assumption that stakeholders will maintain the ledger’s security because their stake will devaluate in case of distrust in the system. PoS attacks do not require initial investment in equipment and electricity costs. While PoW attacks may be noticed when an adversary publishes a block in the network competing with the honest nodes to form the longest chain, PoS attacks happen in silence, using private keys that control transactions to sign a block. The higher the stake (transactions or coins), more powerful is the attack (Bentov, Gabizon, & Mizrahi, 2016).
This ‘silent attack’, also called ‘Costless Simulation’, allows miners to perform a ‘stake-grinding’ attack, extending only blocks that will make them the signers of the next block and thus taking control of the blockchain or creating multiple blockchains because it is cheap to create ‘history’. Because it is not possible to differentiate realtime from blocktime, new users cannot tell when those multiple versions of the blockchain were created: to them, all versions are true. Only existing nodes from before the attack would be able to distinguish those multiple versions of history (Poelstra, 2015).
Decred Project approach
Decred increases PoW security by adding PoS to the mining process. An attacker with a fraction of the tickets would require a number of times the hashpower of honest miners to take over the network. By comparison, an attacker that had the same hashpower of the honest nodes (50% of total hashpower) would still need also 50% of the tickets to successfully attack the network, which is a sizable ‘skin in the game’ for an attacker.
Theoretically, if the minority chain with only a small fraction of tickets had a number of times more hashpower, they could keep up with the majority chain although this is unrealistic because of the economic incentives. Spending a number of times more electricity to obtain the same outcome would turn the reward in 1/n (Collins, 2017).
Other attacks, like the Miner’s Dilemma (Eyal, 2015), those perpetrated by governments, Denial-of-Service attacks, which are based on the isolation of honest nodes among dishonest nodes to facilitate double-spending, the Sybil attack (Eyal & Sirer, 2014), where an adversary creates multiple identities or nodes, and incentives for miners not to propagate to other nodes the received transactions are out of the scope of this inquiry.
Karakostas et. al. tried to define the concept and measure the ‘egalitarianism’ of cryptocurrencies reward by evaluating Decred (PoW+PoS); Bitcoin, Litecoin, Ethereum, Monero (PoW); and the Ouroboros PoS algorithm from Cardano. They created a simulation3 to evaluate minimum required investment size, coinbase rewards, electricity prices, block difficulty, ASIC device specifications and coin prices (Karakostas, Kiayias, Nasikas, & Zindros, 2019). Their findings show a result pointing that Proof-of-Stake blockchains are more ‘egalitarian’ in terms of minimum/multiple size of investment for a stakeholder.
For Decred, they conclude that “egalitarianism is harmed for capitals which are not multiples of ticket prices” but they did not account for Decred Ticket Splitting, which is currently in beta stage and allows multiple participants to buy a ticket spending a minimum of 5 DCRs (in contrast with ticket prices above 100 DCRs since January 2019). Voting rights “are assigned pseudorandomly to a single participant, based on the percentage of their contribution. i.e., if someone purchases 60% of a split ticket, they have a 60% chance of being selected as the voter for that ticket” (Decred Project, 2019). They argue that “perfect egalitarianism could in principle be achieved by making the ticket price approach 0”, which in a ‘one coin one vote’ system would lead to a linear increase in votes and stakeholder power. In the end, they reach a conclusion that Ouroboros and Decred are more ‘egalitarian’ but they did not account for the previously discussed (in)security of pure Proof-of-Stake blockchains, like Ouroboros PoS algorithm from Cardano (Karakostas, Kiayias, Nasikas, & Zindros, 2019, p. 17).
Decred Privacy and Proof-of-Stake mining
Decred Privacy mechanism uses CoinShuffle++4, a protocol used in the mixing process, which builds on top of the ticket purchasing transactions of PoS mining, allowing stakeholders to purchase tickets anonymously. Ticket purchases provide a steady flow of transactions that can be used to mix transaction inputs and completely anonymise the output addresses. Additional work is necessary to obfuscate transaction amounts, and this is why smaller fixed denominations are used (Yocom-Piatt, 2019). The ability to monitor the electoral process using a timestamped audit trail to verify the vote without identifying the voter can increase transparency and participation in the voting process (Johnson, 2019).
On-chain and off-chain governance and decentralisation
The decentralised nature of Bitcoin has already been challenged in the past in a block size dispute, where estimates showed that Chinese miners controlled 74.5% of the network through mining pools. In 2015, developer groups failed to reach consensus over the decision to increase the block size from 1MB to 8MB. While those in favour argued for scalability of the network, those against argued that it would be a huge security risk because it would exclude less powerful machines from handling the blockchain (De Filippi & Loveluck, 2016).
While on-chain governance involves rules and decision-making process encoded in the blockchain, off-chain governance involves all other decisions related to the development and management of a project (Reijers, Wuisman, Mannan, & De Filippi, 2018). Decred Project implements the well-known on-chain5 governance, to maintain consensus rules6, as well as an off-chain governance, using the Politeia governance platform and a timestamping client/server architecture.
Decred Timestamping
Timestamping is the base of the blockchain digital notary and of Politeia off-chain governance system and dcrtime is the client/server application that hashes the content of a file and anchors this hash in the blockchain, proving its existence at a point in time. If the selected file has already been hashed, dcrtime (frontend time client) will show information about that file. Otherwise, the file hash will be published in Decred blockchain in the next hour. Decred offers this functionality for free every hour at dcrtime (backend time server) website7 and also provides the source code.
Politeia
Politeia8 is the censorship-resistant blockchain-anchored public proposal system. Through Politeia anonymous users may propose changes to the development and management of the project, including initiatives to spend the network fund. They can use the platform to debate the proposals, but debates can take place anywhere on the Internet. Statistics9 about proposals can be looked up on the block explorer. The platform and its proposal repository are open source and every proposal receives a token that can be used to prove censorship, in case an administrator needs to remove illegal or nonconforming content. Politeia uses dcrtime to timestamp a proposal and anchor it to the blockchain.
Decentralised Autonomous Organisation (DAO)
A Decentralised Autonomous Organisation (DAO) is a “code-based system with internal capital that lives on the blockchain and operates autonomously (…) through a set of code-based rules (“smart contracts”) to automatically execute payments when certain conditions are met” (Reijers, Wuisman, Mannan, & De Filippi, 2018, pp. 5, 6).
Decred Project plans to create a DAO to enable direct sovereignty over the protocol for a truly decentralised organisation. A DAO can be implemented in two ways: through direct or delegated voting. Delegated voting is like representative democracy (with its well-known issues) and direct voting involves debating proposals, casting votes and living with the consequences of the decisions made. Through Politeia the individuals have a voice and participate in the DAO, having direct sovereignty (Yocom-Piatt, 2019).
The next section will assess blockchain governance, including the mechanisms implemented by Decred Project to increase governance and security.
Footnotes
1 Available at https://docs.decred.org/advanced/issuance/
2 PoS Voting General FAQ, questions 5 and 6, available at https://docs.decred.org/faq/proof-of-stake/general/
3 The source code is available at https://github.com/decrypto-org/egalitarianism
4 From “P2P Mixing and Unlinkable Bitcoin Transactions”, available at https://eprint.iacr.org/2016/824.pdf
5 Available at https://voting.decred.org/
6 Available at https://docs.decred.org/governance/consensus-rule-voting/overview/
7 Available at https://timestamp.decred.org/
8 Available at https://proposals.decred.org/
9 Available at https://dcrdata.decred.org/proposals
References
Bentov, I., Gabizon, A., & Mizrahi, A. (2016, August 31). Cryptocurrencies Without Proof of Work. Financial Cryptography and Data Security, pp. 142-157. Retrieved from: https://link.springer.com/chapter/10.1007/978-3-662-53357-4_10
Bentov, I., Lee, C., Mizhari, A., & Rosenfeld, M. (2014, December 8). Proof of Activity: Extending Bitcoin’s Proof of Work via Proof of Stake. (G. Casale, Ed.) ACM SIGMETRICS Performance Evaluation Review, 42(3). Retrieved from: https://dl.acm.org/doi/10.1145/2695533.2695545
Decred Project. (2016). Decred Constitution. Retrieved from Decred Project: https://docs.decred.org/governance/decred-constitution/
Decred Project. (2019). Ticket Splitting. Retrieved from Decred Documentation: https://docs.decred.org/proof-of-stake/ticket-splitting/
Decred Project. (2020). Proof-of-Stake (PoS) Voting. Retrieved from Decred Docs: https://docs.decred.org/proof-of-stake/overview/
De Filippi, P., & Loveluck, B. (2016, October 17). The Invisible Politics of Bitcoin: Governance Crisis of a Decentralized Infrastructure. Internet Policy Review, 5(4). Retrieved from: https://ssrn.com/abstract=2852691
Eyal, I. (2015, July 20). The Miner’s Dilemma. 2015 IEEE Symposium on Security and Privacy (pp. 89-103). San Jose, CA: IEEE. Retrieved from https://ieeexplore.ieee.org/abstract/document/7163020
Eyal, I., & Sirer, E. (2014, November 09). Majority Is Not Enough: Bitcoin Mining Is Vulnerable. Financial Cryptography and Data Security. FC 2014, 8437 (Lecture Notes in Computer Science), 436-454. Retrieved from: https://link.springer.com/chapter/10.1007/978-3-662-45472-5_28
Johnson, D. (2019, September 18). Blockchain-Based Voting in the US and EU Constitutional Orders: A Digital Technology to Secure Democratic Values? European Journal of Risk Regulation, 10(2), 330–358. Retrieved from: https://doi.org/10.1017/err.2019.40
Kalomeni, M. (2018, September 27). The ICO market is not collapsing. It’s maturing. Retrieved from Elementus: https://elementus.io/blog/ico-market-august-2018/
Karakostas, D., Kiayias, A., Nasikas, C., & Zindros, D. (2019). Cryptocurrency Egalitarianism: A Quantitative Approach. Tokenomics 2019. Retrieved from: https://arxiv.org/abs/1907.02434
Martins, M. (2018, July 24). The origin of Decred. Retrieved from Stakey Club: https://stakey.club/en/the-origin-of-decred/
Poelstra, A. (2015, March 22). On Stake and Consensus. Retrieved from Satoshi Nakamoto Institute: https://nakamotoinstitute.org/static/docs/on-stake-and-consensus.pdf
Reijers, W., Wuisman, I., Mannan, M., & De Filippi, P. (2018, December 18). Now the Code Runs Itself: On-Chain and Off-Chain Governance of Blockchain Technologies. TOPOI : International Review of Philosophy, 37(17). Retrieved from Springer Link: https://link.springer.com/article/10.1007/s11245-018-9626-5
Yocom-Piatt, J. (2019, November 19). Cointelegraph. Secrets They Missed at DevCon: What It’s Really Like in a Working DAO. Retrieved from: https://cointelegraph.com/news/secrets-they-missed-at-devcon-what-its-really-like-in-a-working-dao