Geração de chaves no Decred
Este artigo fornece uma explicação mais detalhada e técnica do processo de geração de chaves no Decred e demonstra como esse processo gera endereços seguros e privados. Não é necessário conhecer esse mecanismo interno para entender ou usar criptomoedas com segurança. Mas, por mais técnico e tedioso que possa ser esse assunto, compreender como funcionam algumas engrenagens, além de matar a curiosidade, nos dá mais segurança por entender melhor como algumas coisas funcionam.
Não há necessidade de tratar aqui do funcionamento interno de algoritmos de hash. Para se aprofundar mais, veja os links nas referências.
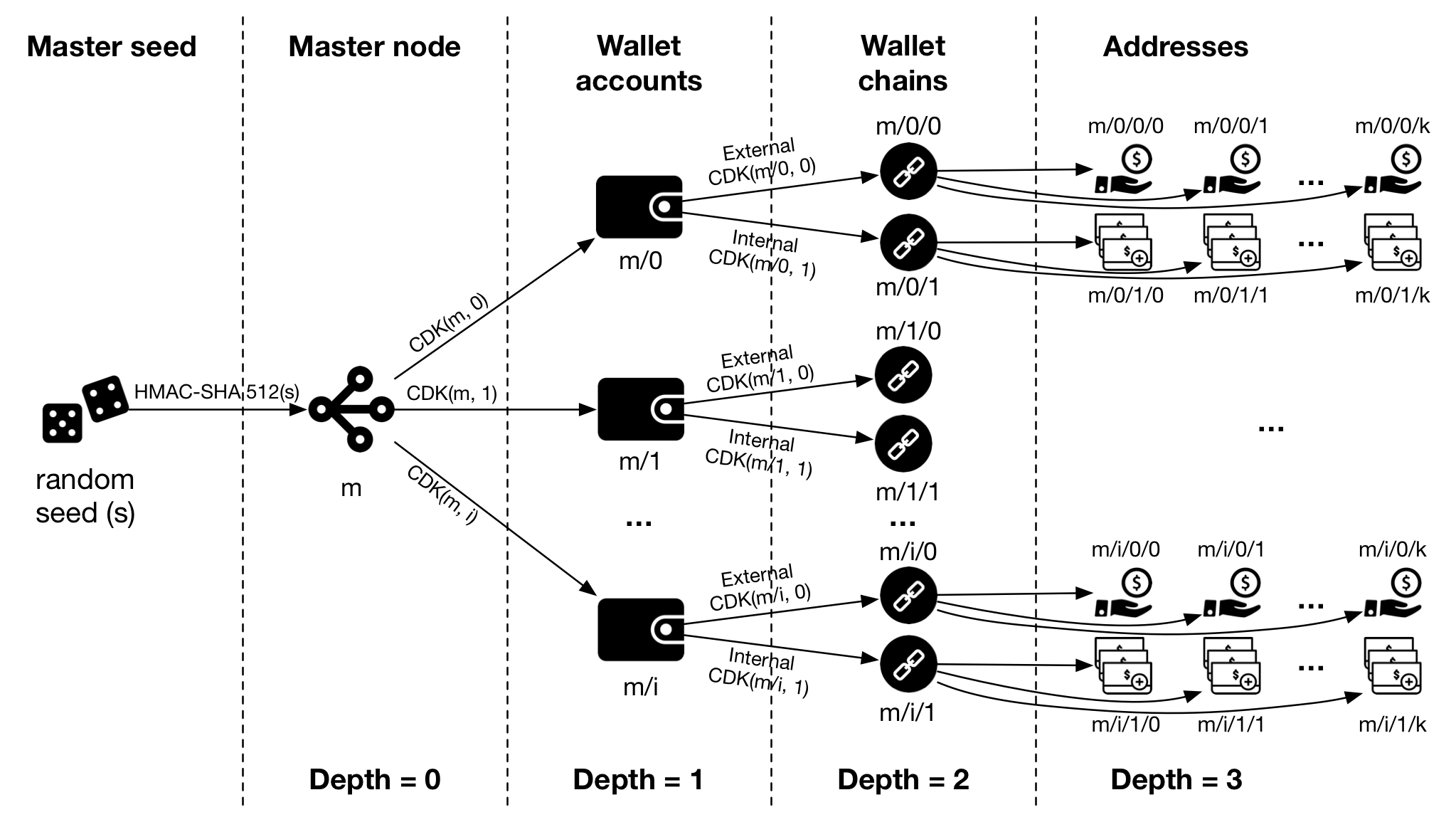
Figura 1 - A estrutura de chaves derivadas a partir da chave privada (Rebuilt from Bitcoin Mediawiki)
1. Geração de endereços
1.1. Geração da Seed
// GenerateSeed returns a cryptographically secure random seed that can be used // as the input for the NewMaster function to generate a new master node. // // The length is in bytes and it must be between 16 and 64 (128 to 512 bits). // The recommended length is 32 (256 bits) as defined by the RecommendedSeedLen // constant.
[único componente de aleatoriedade]
1.2. Geração do Master Node
One master node (seed) can be used for unlimited number of independent cryptocoins such as Bitcoin, Litecoin or Namecoin. However, sharing the same space for various cryptocoins has some disadvantages.This level creates a separate subtree for every cryptocoin, avoiding reusing addresses across cryptocoins and improving privacy issues.Coin type is a constant, set for each cryptocoin. Cryptocoin developers may ask for registering unused number for their project.The list of already allocated coin types is in the chapter “Registered coin types” below.Hardened derivation is used at this level.
1.3. Geração da Wallet account
This level splits the key space into independent user identities, so the wallet never mixes the coins across different accounts.
Users can use these accounts to organize the funds in the same fashion as bank accounts; for donation purposes (where all addresses are considered public), for saving purposes, for common expenses etc.
Accounts are numbered from index 0 in sequentially increasing manner. This number is used as child index in BIP32 derivation.
Hardened derivation is used at this level.
Software should prevent a creation of an account if a previous account does not have a transaction history (meaning none of its addresses have been used before).
Software needs to discover all used accounts after importing the seed from an external source. Such an algorithm is described in “Account discovery” chapter.
1.4. Geração da Wallet Chain
Constant 0 is used for external chain and constant 1 for internal chain (also known as change addresses). External chain is used for addresses that are meant to be visible outside of the wallet (e.g. for receiving payments). Internal chain is used for addresses which are not meant to be visible outside of the wallet and is used for return transaction change.
1.5. Geração do endereço externo (pagamento)
Addresses are numbered from index 0 in sequentially increasing manner. This number is used as child index in BIP32 derivation.Public derivation is used at this level.
1.6. Geração do endereço interno (troco)
aaa
1.7. Base58Check
Base58 is a group of binary-to-text encoding schemes used to represent large integers as alphanumeric text. It is similar to Base64 but has been modified to avoid both non-alphanumeric characters and letters which might look ambiguous when printed. It is therefore designed for human users who manually enter the data, copying from some visual source, but also allows easy copy and paste because a double-click will usually select the whole string.
Compared to Base64, the following similar-looking letters are omitted: 0 (zero), O (capital o), I (capital i) and l (lower case L) as well as the non-alphanumeric characters + (plus) and / (slash).
Base58Check is a Base58 encoding format that unambiguously encodes the type of data in the first few characters and includes an error detection code in the last few characters.
2. Account discovery
When the master seed is imported from an external source the software should start to discover the accounts in the following manner:
derive the first account’s node (index = 0) derive the external chain node of this account scan addresses of the external chain; respect the gap limit described below if no transactions are found on the external chain, stop discovery if there are some transactions, increase the account index and go to step 1 This algorithm is successful because software should disallow creation of new accounts if previous one has no transaction history, as described in chapter “Account” above. Please note that the algorithm works with the transaction history, not account balances, so you can have an account with 0 total coins and the algorithm will still continue with discovery.
2.1. Gap address limit
Address gap limit is currently set to 20. If the software hits 20 unused addresses in a row, it expects there are no used addresses beyond this point and stops searching the address chain. We scan just the external chains, because internal chains receive only coins that come from the associated external chains. Wallet software should warn when the user is trying to exceed the gap limit on an external chain by generating a new address.
Addresses
“I’ve explained it elsewhere, but a Decred address is actually just a representation of a public key (which itself could be a script hash) along with a 2-byte prefix which identifies the network and type and a checksum suffix in order to detect improperly entered addresses.
Consequently, as the params I linked show, you can always tell what type of address it is based on the 2-byte prefix.
The first byte of the prefix identifies the network. This is why all mainnet addresses start with “D”, testnet addresses start with “T”, and simnet addresses start with “S”. The second byte of the prefix identifies the type of address it is.
The most common addresses used at the moment are secp256k1 pubkey hashes, which are identified by a lowercase “s”. It represents a single public key and therefore only has a single associated private key which can be used to redeem it.
The stake pool, however, uses a pay-to-script-hash address, which is identified by the second byte being a lowercase “c” (again that is shown in the linked params). The specific flavor of script it generates is a multi-signature 1-of-2, which is how it allows either the pool, or you, to vote. Both you and the stake pool have your own private keys and since the script only requires one signature of the possible two, that is how it allows delegation of voting rights to the pool without you giving up your voting rights completely.”
–davecgh
Referências: