Decred via Tor network
1. Introduction
Tor is a network of devices voluntarily maintained by individuals interested in privacy and security. Tor allows a person to access content through a series of encrypted virtual tunnels between their participants to avoid censors and the disclosure of their location.
Through Tor journalists and whistleblowers disseminate information, organizations fight for freedom and make complaints while operating from inside a dictatorship and individuals maintain their privacy and access content blocked by their local providers.
Tor’s network can also be used to connect cryptocurrency peers in countries where the State wants to maintain control over money and pursues those seeking financial freedom.
Prerequisites
a) Download Tor from the Tor Project website.
b) Below the download button there is a sig link to download the digital signature. Download the signature and verify it as instructed here.
c) Tor does not need to be locally installed, and may be extracted to a directory and executed.
Learn more about the Verifying Digital Signatures.
2. Pluggable transports
Despite the usage of several different bridges (devices that connect to the Internet and Tor network simultaneously) to avoid censor blocking, there has been an increase in the number of countries that use Deep Packet Inspection (DPI) to recognize and filter such packets, even when IP addresses not yet related to the Tor network are used.
obfs4
Obfs4 is an obfuscation layer for TCP protocols designed to prevent third parties from inferring which protocol is being obfuscated from the message content or format.
After handshake and key exchange the data will be encrypted and authenticated in smaller frames through a crypto_secretbox_xsalsa20poly1305 function.
The complete obfs4 specification can be accessed at https://github.com/Yawning/obfs4/blob/master/doc/obfs4-spec.txt.
meek
Meek, like obfs4, introduces a layer of obfuscation to avoid censors on the Internet. Traffic is directed to another server through a technique called Domain Fronting, which bridges the user to the server that is being censored.
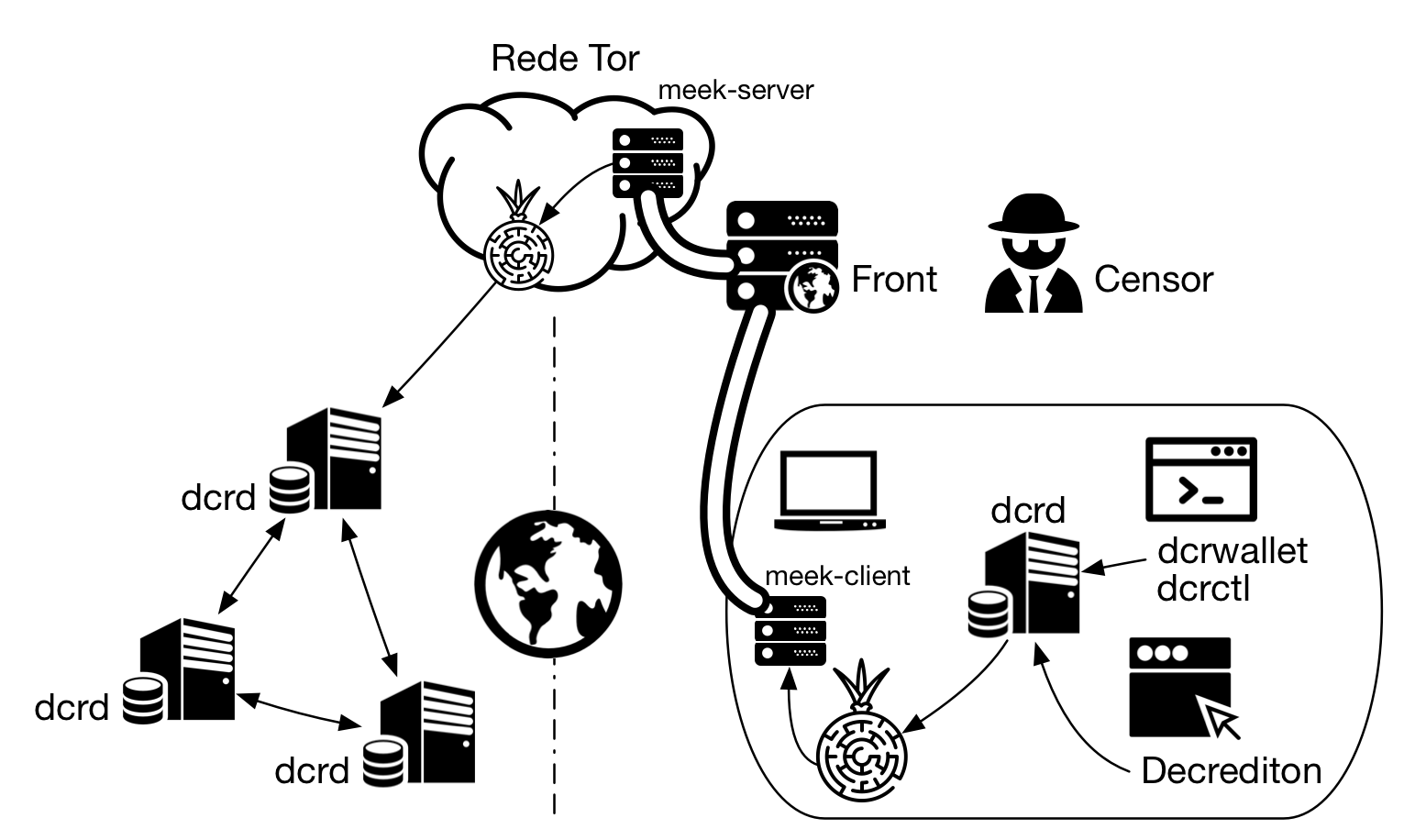
Figure 1 - meek with local dcrd or Decrediton's internal dcrd
A figura a seguir mostra o cenário apresentado no artigo Decred através de VPNs e proxies, onde um servidor dcrd é hospedado e acessado remotamente. Além das formas de acesso apresentadas naquele artigo, esse servidor também pode ser acessado através de Tor com o pluggable transport do meek.
Domain Fronting consists in encapsulating an HTTP packet into a TLS packet destined for a domain other than the original. The meek-client creates an HTTPS packet that is sent to an intermediate server, which spans many domains, such as a Content Distribution Network (CDN). This intermediate domain (“front domain”) has its address clearly included in the package, unencrypted. The packet to be sent to the censored domain is encrypted within the external packet, referenced via Host Header. The censor can only see the unencrypted information in the external packet, but the CDN can see the inner packet, reads the host header and forwards the packet to the destination server. There meek-server decrypts the packet and directs the data to the Tor network.
Any domain with a CNAME record pointing to the CDN of a major provider such as Cloudfront, for example, can be used as an input channel:
$ dig cdn.bitnami.com
(...)
;; ANSWER SECTION:
cdn.bitnami.com. 10800 IN CNAME d33np9n32j53g7.cloudfront.net.
d33np9n32j53g7.cloudfront.net. 12 IN A 216.137.61.47
d33np9n32j53g7.cloudfront.net. 12 IN A 216.137.61.97
d33np9n32j53g7.cloudfront.net. 12 IN A 216.137.61.216
d33np9n32j53g7.cloudfront.net. 12 IN A 216.137.61.149
d33np9n32j53g7.cloudfront.net. 12 IN A 216.137.61.82
d33np9n32j53g7.cloudfront.net. 12 IN A 216.137.61.59
d33np9n32j53g7.cloudfront.net. 12 IN A 216.137.61.78
d33np9n32j53g7.cloudfront.net. 12 IN A 216.137.61.154
(...)
Services that can provide “fronting” are Google App Engine and Microsoft Azure. Amazon CloudFront has decided to prevent domain fronting from working on your network. The goal is to choose a large content provider that the censor does not want to block, otherwise it would do great harm to the censor itself (legitimate business would be blocked, loss of contact with partners, loss of tax revenue due to disruption of local services, etc). The “front domain” server may be located on or off the censor-controlled network. Two major content providers listed in Tor’s bridge_prefs.js file are a0.awsstatic.com and ajax.aspnetcdn.com. The following figure shows the package encapsulation between meek-client and meek-server.
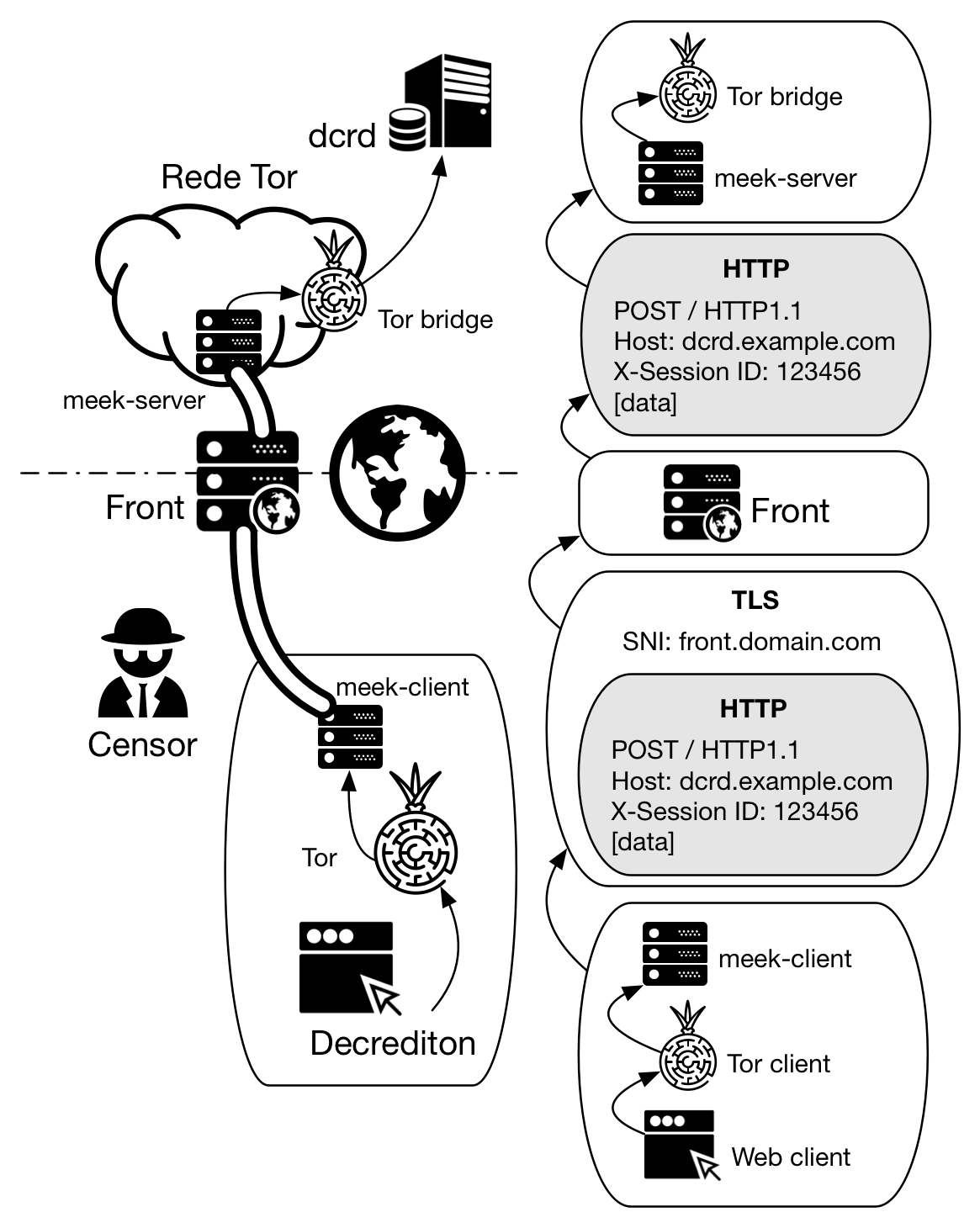
Figure 3 - TLS encapsulation made by meek
3. dcrd configuration and Tor
Dcrd may work anonymously or not while connected to the Tor network. How it works depends on the parameters that will be explained in this section.
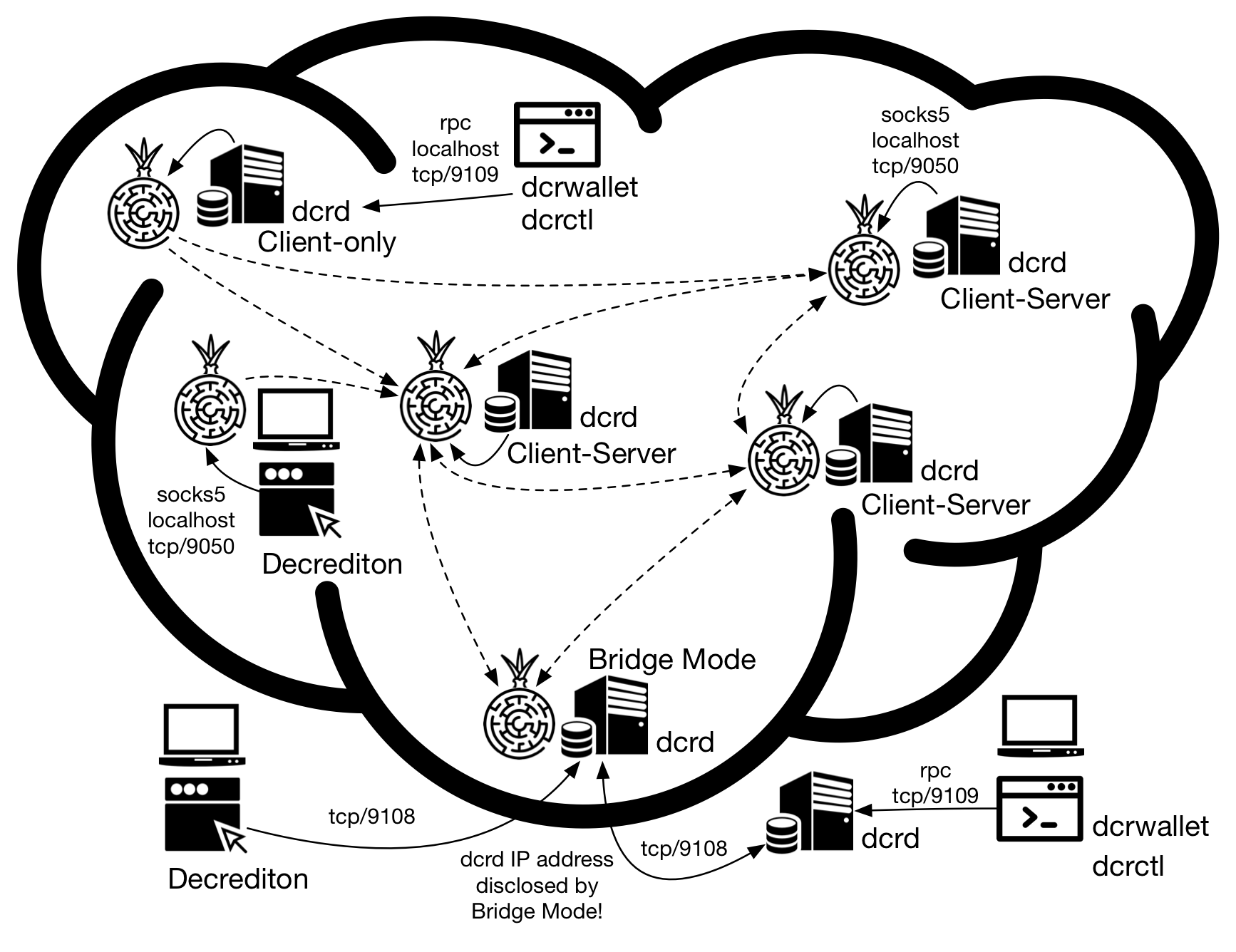
Figure 4 - Some Tor usage scenarios
3.1. Client-only
When configured as client-only, dcrd will only check for blockchain updates (new blocks and mempool transactions) on other servers but there will be no way for other servers to connect to dcrd to check for updates.
To run dcrd as a Tor client:
$ ./dcrd --proxy=127.0.0.1:9050
To permanently configure Tor in dcrd.conf, add to the [Application Options] section:
proxy=127.0.0.1:9050
If Tor has been set to prompt for username and password, you will need to enter them using --proxyuser and --proxypass at the command line or in the configuration file.
By default, dcrd assumes that this specified proxy is a Tor network proxy and sends all traffic, including queries for DNS name resolution, through this specified proxy.
3.2. Client-Server via Tor Onion Service
Client-Server configuration allows other dcrd servers to connect to your dcrd for block update and mempool transactions. This configuration makes Decred network more robust and for this reason is the recommended configuration.
To install the Onion Service, you will need to edit a file named torrc.
a) On Linux and Windows, navigate to the Browser/TorBrowser/Data/Tor/torrc directory in the Tor Browser directory. In macOS, navigate to the ~/Library/Application Support/TorBrowser-Data/Tor directory.
b) Open file torrc and search for the line: ### This section is just for location-hidden services ###
c) Add the following lines to torrc:
HiddenServiceDir /var/tor/dcrd
HiddenServicePort 9108 127.0.0.1:9108
d) Save the torrc file and restart Tor. If Tor restarts it is working and you have automatically created the directory specified in HiddenServiceDir. Otherwise, something went wrong. Start by looking at the log files to see what happened.
3.2.1. hostname
The file hostname is created by Tor and contains the name with which the service advertises on the Tor network, which is a short version of the public key and looks like duskgytldkxiuqc6.onion. This is the public name of your service and will be used in the dcrd setup.
3.2.2. private_key
Another file created in the same directory is private_key. Keep it safe! It contains the private key generated for this onion service and if it gets the wrong hands it will allow third parties to impersonate you on the Tor network.
To run dcrd in Client-Server mode:
$ ./dcrd --proxy=127.0.0.1:9050 --listen=127.0.0.1 --externalip=$HOSTNAME.onion
To permanently configure the dcrd.conf file, add to the [Application Options] section:
proxy=127.0.0.1:9050
listen=127.0.0.1
externalip=$HOSTNAME.onion
If Tor has been configured to prompt for username and password, you will be prompted for them using the --proxyuser and --proxypass parameters in the command line or configuration file.
3.3. Bridge Mode
Dcrd can bridge nodes inside and outside the Tor network. Only traffic sent to and from the .onion address will travel on the Tor network and the rest of the traffic will be sent normally, resulting in non-anonymous traffic.
This mode works only if the --onion parameter is used. If it is necessary to set username and password it should be done using the --onionuser and --onionpass parameters.
To run dcrd in bridge mode:
$ ./dcrd --onion=127.0.0.1:9050 --externalip=$HOSTNAME.onion
To set permanently in the dcrd.conf file, add to the [Application Options] section:
onion=127.0.0.1:9050
externalip=$HOSTNAME.onion
4. Decred clients configuration
4.1. Decrediton
To make Decrediton use Tor, locate and open the dcrd.conf file according to your operating system:
Linux: ~/.config/decrediton
macOS: ~/Library/Application Support/Dcrd
Windows: C:\Users\$USERNAME\AppData\Local\Decrediton
and add the following line to the [Application Options] section:
proxy=127.0.0.1:9050
If Tor has been configured to prompt for username and password, you will be prompted for them using the --proxyuser and --proxypass parameters in the command line or configuration file.
Decrediton connects to its own dcrd. No further configuration is required.
4.2. dcrwallet
According to the comments inside sample-dcrwallet.conf file, you can configure dcrwallet to connect to the RPC server via Tor in the “RPC client settings” section. Add or uncomment the following parameters:
proxy=127.0.0.1:9050
rpcconnect=$HOSTNAME.onion:9109
This setting is useful when connecting dcrwallet to a dcrd located on the other side of a cryptographic tunnel.
5. Tor Stream Isolation
Tor stream isolation forces Tor to create new circuits for each connection making identity correlation more difficult.
Dcrd supports Tor stream isolation through the --torisolation parameter. This parameter requires --proxy or --onionproxy parameters to be used. To execute at the command line:
$ ./dcrd --proxy=127.0.0.1:9050 --torisolation
To permanently configure this setting in dcrd.conf:
[Application Options]
proxy=127.0.0.1:9050
torisolation=1
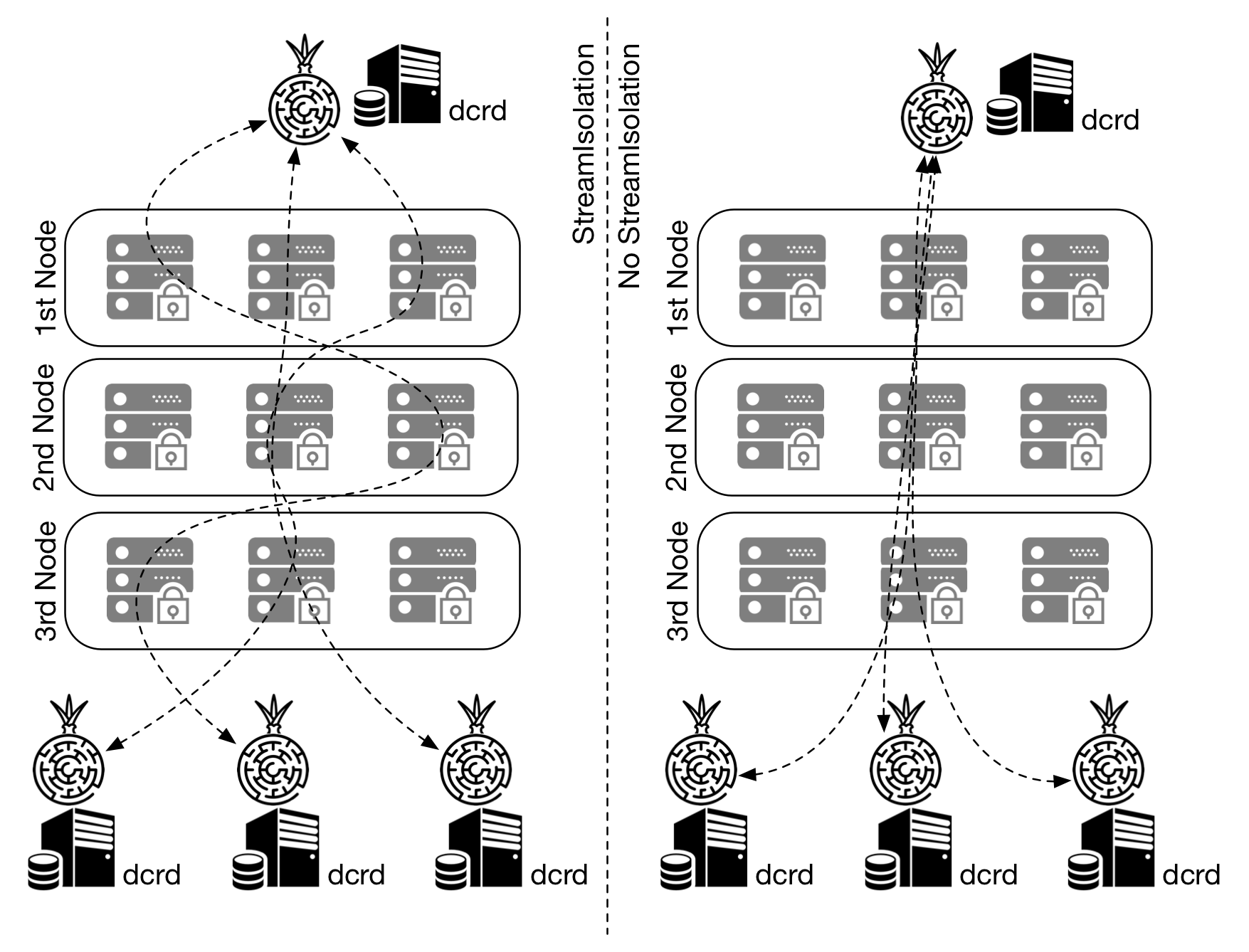
Figure 5 - Path taken by information, with and without Stream Isolation
To learn more about Stream Isolation:
- https://www.torproject.org/docs/tor-manual.html.en
- https://tails.boum.org/contribute/design/stream_isolation/
- https://www.whonix.org/wiki/Stream_Isolation
References: This article contains a lot of information from https://github.com/decred/dcrd/blob/master/docs/configuring_tor.md and https://www.torproject.org/docs/tor-onion-service.